Table of content
The cyber kill chain is a cybersecurity framework developed to map how attackers move through a network. In 2025, it remains critical for understanding and defending against modern cyber threats. This systematic approach helps organisations detect and disrupt attacks at multiple stages:
- Reconnaissance – Initial target research
- Weaponisation – Creating malicious payloads
- Delivery – Transmitting attacks to targets
- Exploitation – Executing vulnerabilities
- Installation – Establishing persistent access
- Command and Control – Maintaining communications
- Actions on Objectives – Achieving attack goals
Originally developed by Lockheed Martin in 2011, this framework has evolved to address contemporary threats, including cloud environments, mobile devices, and advanced social engineering campaigns. As recent cyberattacks, such as the M&S incident, demonstrate, organisations need robust cybersecurity frameworks more than ever.
Quick Reference: The 7 Stages of the Cyber Kill Chain
| Stage | Description | Example | Key Defences |
|---|---|---|---|
| Reconnaissance | Research & identify vulnerabilities | Social media, public records | Information security policies, monitoring |
| Weaponisation | Develop an exploit or a payload | Malware creation | Threat intelligence, vulnerability management |
| Delivery | Send to target | Phishing, malicious links | Email security, web filtering |
| Exploitation | Execute the exploit to gain access | Buffer overflow, privilege escalation | Patch management, behavioural monitoring |
| Installation | Establish persistence | Backdoors, registry edits | Application whitelisting, integrity checking |
| Command & Control | Maintain communications | C2 channels via HTTPS | Network monitoring, DNS filtering |
| Actions on Objectives | Achieve attack goals | Data theft, system disruption | Data loss prevention, privileged access management |
What is the Cyber Kill Chain?
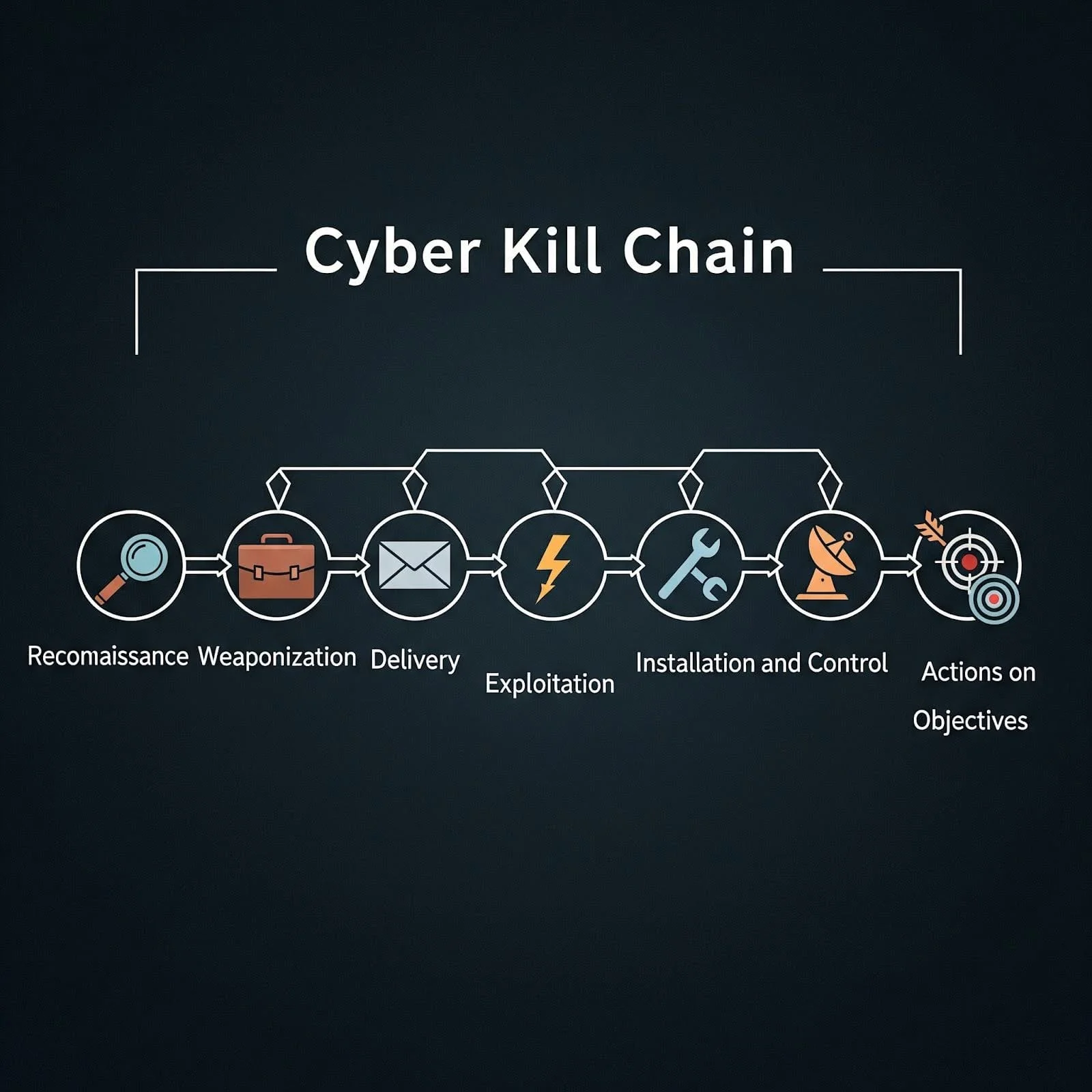
The cyber kill chain is a framework developed by Lockheed Martin that describes the stages of a cyber attack from initial reconnaissance to final objectives. This cybersecurity model provides security teams with a systematic approach to understanding how attackers operate and where defensive measures can be most effective.
The concept borrows from military terminology, where a “kill chain” refers to the sequence of events that comprise an attack, from target identification to engagement. In cybersecurity, the cyber kill chain maps the adversary’s progression through a network, helping defenders identify attack patterns and implement appropriate countermeasures at each stage.
Why It Matters in 2025:
- Enhanced threat detection capabilities
- Improved incident response planning
- Better security architecture design
- More effective threat hunting operations
Understanding these frameworks is crucial for modern businesses, especially when considering how technical debt can create additional security vulnerabilities in your systems.
What are the 7 Stages of the Cyber Kill Chain?
1. Reconnaissance
The first stage involves gathering information about the target organisation. During this phase, attackers collect data about the company’s infrastructure, employees, technologies, and potential vulnerabilities. This intelligence gathering can take weeks or months and often involves passive techniques that are difficult to detect.
Common Techniques:
- Social media research
- Public records analysis
- Network scanning
- Social engineering
Key Defences at this Stage:
- Implement information security policies
- Conduct employee awareness training
- Monitor for suspicious reconnaissance activities
- Limit public information exposure

2. Weaponisation

Attackers create malicious payloads designed to exploit identified vulnerabilities. This phase involves combining exploits with backdoor code to create deliverable payloads. The sophistication of weaponisation often indicates the skill level and resources of the attacking group.
Common Techniques:
- Creating malicious documents
- Developing custom malware
- Preparing exploit kits
- Testing payloads against target environments
Key Defences at this Stage:
- Threat intelligence monitoring
- Vulnerability management programmes
- Security awareness about emerging threats
- Proactive threat hunting
3. Delivery
The delivery phase focuses on transmitting the weaponised payload to the target environment. This stage represents the transition from preparation to active attack and is often where organisations have the best opportunity to detect and block attacks.
Common Techniques:
- Email attachments
- Malicious websites
- USB devices
- Supply chain compromises
Key Defences at this Stage:
- Email security solutions
- Web filtering and proxy controls
- Endpoint protection platforms
- Application control policies

4. Exploitation
The delivered payload executes and takes advantage of system vulnerabilities. This stage marks the beginning of active compromise and involves various techniques depending on the target environment and attack objectives.
Common Techniques:
- Buffer overflow attacks
- Privilege escalation
- Application vulnerabilities
- Zero-day exploits
Key Defences at this Stage:
- Regular patch management
- Configuration hardening
- Behavioural monitoring
- Runtime application protection
5. Installation
Attackers establish persistent access to the compromised system by installing backdoors, creating user accounts, or modifying system configurations. This phase often involves anti-forensics techniques to avoid detection.
Common Techniques:
- Registry modifications
- Service creation
- Scheduled task establishment
- Rootkit installation
Key Defences at this Stage:
- Application whitelisting
- System integrity monitoring
- Behavioural analysis
- Privilege access management
6. Command and Control (C2)
This phase establishes communication channels between the compromised system and the attacker-controlled infrastructure. Modern attacks often use legitimate services and encrypted communications to avoid detection.
Common Techniques:
- HTTP/HTTPS communications
- DNS tunnelling
- Custom protocols
- Cloud service abuse
Key Defences at this Stage:
- Network traffic monitoring
- DNS filtering
- Proxy controls
- Anomaly detection
7. Actions on Objectives
The final stage involves achieving the attacker’s ultimate goals, whether data exfiltration, system disruption, or other malicious activities. This represents the culmination of the entire attack process.
Common Objectives:
- Intellectual property theft
- Financial fraud
- Espionage
- Destructive attacks
Key Defences at this Stage:
- Data loss prevention
- Continuous monitoring
- Incident response procedures
- Backup and recovery systems
Why is the Cyber Kill Chain Important in 2025?
The cyber kill chain remains highly relevant because it helps organisations:
- Detect threats earlier by understanding attack progression
- Align defences to specific attack stages
- Improve incident response through structured analysis
- Enhance threat hunting with systematic approaches
- Build layered security that creates multiple failure points for attackers
Modern interpretations integrate with frameworks like MITRE ATT&CK to provide more granular attack analysis while maintaining the strategic overview that makes the kill chain valuable.

What’s the Difference Between the Cyber Kill Chain and MITRE ATT&CK?
While both frameworks analyse cyber attacks, they serve different purposes:
Cyber Kill Chain:
- Linear, conceptual framework
- High-level strategic view
- Seven broad stages
- Excellent for planning and communication
MITRE ATT&CK:
- Detailed matrix of tactics and techniques
- Specific, actionable intelligence
- Hundreds of documented techniques
- Better for operational security teams
Real-World Cyber Kill Chain Examples
Example 1: Advanced Persistent Threat Campaign
Reconnaissance: Attackers research pharmaceutical company employees on LinkedIn, identifying key personnel and technology stack information.
Weaponisation: Based on findings, attackers create a malicious Microsoft Office document exploiting a known vulnerability.
Delivery: The document is sent via spear-phishing email to targeted employees.
Exploitation: When opened, the document exploits a memory corruption vulnerability to execute code.
Installation: The exploit installs a persistent backdoor that survives reboots.
Command and Control: The backdoor establishes encrypted HTTPS communication with attacker servers.
Actions on Objectives: Attackers navigate the network and exfiltrate sensitive research data over months.
Example 2: Retail Breach (Target-style Attack)
This type of attack demonstrates how attackers can move from initial compromise through a retail network to achieve data theft objectives, highlighting the importance of network segmentation and continuous monitoring.
Implementing Cyber Kill Chain Defence Strategies
Organisations can leverage this framework to build comprehensive defence strategies addressing each attack stage:
Multi-Stage Defence Approach
Early Stage Defences (Reconnaissance – Delivery):
- Information security policies
- Employee training programmes
- Email and web security
- Threat intelligence integration
Mid-Stage Defences (Exploitation – Installation):
- Patch management
- Endpoint detection and response
- Application security
- Behavioural monitoring

Late-Stage Defences (C2 – Actions on Objectives):
- Network segmentation
- Data loss prevention
- Privileged access management
- Incident response procedures
For startups and SMEs looking to implement these defences, understanding how AI and ML technologies can enhance cybersecurity capabilities is increasingly important.
The Unified Cyber Kill Chain
The Unified Cyber Kill Chain represents an evolution addressing modern attack complexity. This enhanced model:
- Incorporates multiple concurrent attack paths
- Addresses non-linear attack progression
- Integrates feedback loops
- Better represents sophisticated adversary behaviour
- Works with contemporary security frameworks
Is the Cyber Kill Chain Still Relevant Today?
Yes, the cyber kill chain remains highly relevant in modern cybersecurity. While critics argue that attacks don’t always follow linear progression, the framework’s flexibility allows adaptation for:
- Cloud security environments
- Insider threat scenarios
- Advanced social engineering
- Supply chain attacks
- Mobile and IoT threats
The framework continues to evolve and integrate with other security models while maintaining its core value as a strategic planning tool.
Top 5 Takeaways for Cybersecurity Leaders
- Implement layered defences across all kill chain stages rather than relying on single security controls.
- Focus on early detection at reconnaissance and delivery stages, where intervention is most effective
- Integrate threat intelligence to understand weaponisation trends and delivery methods
- Plan incident response using kill chain stages to guide investigation and containment
- Combine frameworks – use kill chain strategically with MITRE ATT&CK operationally
Conclusion
The cyber kill chain framework remains one of the most valuable tools for understanding and defending against cyber attacks. By breaking down attacks into discrete stages, organisations can implement targeted defences and improve their overall security posture.
As cyber threats continue to evolve, the framework adapts to address new attack vectors while maintaining its strategic value. Security professionals who master the cyber kill chain are better equipped to protect their organisations against sophisticated adversaries in an increasingly complex threat landscape.
The continued relevance of this approach in 2025 demonstrates the enduring value of systematic threat analysis and defence planning in modern cybersecurity operations.
Take the first step towards comprehensive cybersecurity protection. Our experts will assess your current security posture and provide actionable recommendations based on proven frameworks like the cyber kill chain.
Don’t let cybercriminals complete their kill chain. Partner with RSVR to build robust defences that protect your organisation at every stage of a potential attack.
Frequently Asked Questions (FAQs)
What is the cyber kill chain?
The cyber kill chain is a framework developed by Lockheed Martin that describes the stages of a cyber attack from initial reconnaissance to final objectives, providing a systematic approach to understanding adversary behaviour and building effective defence strategies.
What are the 7 stages of the cyber kill chain?
The seven stages are: reconnaissance, weaponisation, delivery, exploitation, installation, command and control, and actions on objectives. Each stage represents a distinct phase in attack progression.
What are the 8 phases of the cyber kill chain?
The 8-phase model includes the traditional seven stages plus monetisation, addressing how attackers profit from their activities, particularly relevant for financially motivated cybercriminal organisations.
Is the cyber kill chain still relevant?
Yes, it remains highly relevant in modern cybersecurity. While originally focused on traditional attacks, current applications encompass cloud security, insider threats, and advanced social engineering campaigns. The framework continues to evolve and integrate with other security models.








